Cookies vs Sessions vs Tokens

Are you new to web-development, feeling confused with different Web Storage elements?
If yes, then you are at the right place This article will give you a brief explanation about sessions, cookies and tokens using its authentication techniques.
There are two different authentication techniques namely
- Cookie/Session-based Authentication
- Token-based authentication
What are cookies and sessions?
In simple words, Cookies and Sessions are files used to store information.
How do they differ
- Cookies are text files stored only on the client-side machine, where sessions create a file in a temporary directory on the server to store variables. Variables inside sessions help us to track user activities.
- Cookies get stored in the browser where sessions are not.
- Cookies can keep the information until it gets deleted where sessions get destroyed whenever the user tries to close a browser. Sessions will end by the server over a predetermined period, commonly 30 minutes duration.
- Variables defined inside a cookie helps the user from providing credentials for authentication every time. Variables inside a session help to track the user activity using cookies in the browser.
- Cookies can only store strings where sessions can store in the form of objects (JSON).
- A cookie can store information only up to 4000 bytes (4 KB).
- Cookies get saved in the browser for future reference. The server sends a set of cookies to the browser. For example name, age, or identification number etc. Which helps in latter user authentications. where sessions are completely lost whenever the user closes the browser.
Cookie Based Authentication
To understand this, we need get back to basics. Consider you are going to login to your bank account using website.
On the login page, you have to enter your credentials. Based on the credentials, the server tries to pick up your user record from the database and generates a Session-Id using your credentials. The server will pass session id to the browser to store in cookies. Cookies in our browser help the server to track user activities and helps the user from providing credentials in latter authentications over a period of time.
Whenever the user tries to logout, the server will clear session Id and instructs the browser to destroy the cookie stored during the authentication. This process is called Cookie Based Authentication.
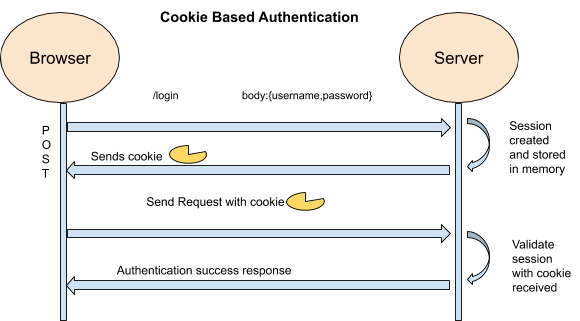
Cookie-based authentication has been the default, tried-and-true method for handling user authentication for a very long time.
Cookie-based authentication is stateful. The term Stateful refers to generating and maintaining the sessions inside the server.
What are Tokens?
Similar to cookies and sessions, tokens used to store user information. Unlike cookies and sessions, Tokens built with optional signature and/or optional encryption with payload holds a small piece of user information in a format of JSON.
Using a private secret or a public/private key, tokens generates it signature. That makes our tokens strong. The tokens get signed by one party’s private key (usually the server’s) so that party can then verify the token is legitimate.
Token-Based Authentication
Although cookie-based authentication is successful. Token-based authentication has gained prevalence over the last few years due to the rise of single-page applications, web APIs, and the Internet of Things (IoT). When we talk about authentication with tokens, we generally talk about authentication with JSON Web Tokens (JWTs).
Consider the same banking application. I need to keep track of daily expenses to control the expenditure. But it’s been difficult for me to remember my day-to-day expenses. Then I found an app in an AppStore that keeps a track of my expenses, which will satisfy my needs.
But we can’t directly give our bank credentials to that app. Instead, the app gets our bank account number that makes a request to our bank server, get access to reading our transaction details.
Our bank server will provide the app access to read our transaction details based on the user’s confirmation.
In this place, using cookie-based authentication will lead us to some CORS (Cross-Origin Resource Sharing) issues.
Tokens saves information only on client-side environments and it will not have any impact on cross platforms(CORS issues).
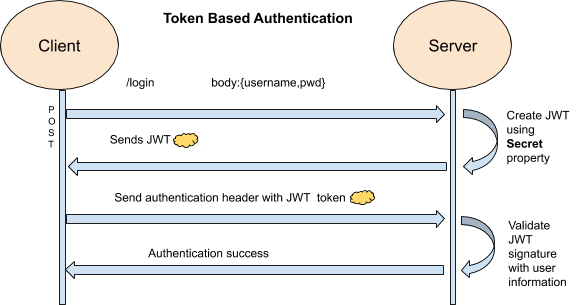
From the above use case, we can conclude that authentication using tokens are far better in cross-platforms over traditional cookie-based authentication.
Token-based authentication is stateless. The server does not keep any record of user activities.
The token is generally sent in the header with a property named Authorization of value Bearer { JWT Token}.
Authorization: Bearer <token>
It can also be attached with the body of a POST request or even as a query parameter.
Advantages of Token-based authentication over Cookie Based Authentication
Stateless
Being Stateless is the most important advantage over cookies, that reduces the load to the server from tracking user activities.
Each token is self-contained, containing all the data required to check it’s validity as well as convey user information through claims.
Client Storage
With a cookie-based approach, you will store only in the form of strings. JWT’s, however, allows you to store any type of metadata, as long as it’s valid JSON.
Web storage API like session-storage and local-storage helps to store tokens in the browser.
Maximum Storage limit of Web API Storage is 10 Mb(Local storage). Using Npm package IdleTimer, we can control the expiration time of Web API storages.
CORS issues
Cookies work well with singular domains and subdomains, but it becomes difficult when it comes to managing cookies across different domains. Through Token-based authentication, we can avoid such errors as its stores token only in the client environment. Which makes it a good choice over cross-platform applications.(Mobile / Web).
Token-Based Authentication using JWT is the more recommended method in modern web apps. One drawback with JWT is that the size of JWT is not much bigger. JSON object in JWT should contain only necessary information and avoid adding sensitive information to prevent XSS security attacks.
Thanks for reading.Happy coding😊.
Comments
Post a Comment